Since we launched the BitBox02, we hear requests to support airgap operation: using the hardware wallet without plugging it into a computer or phone. Air-gapped devices have been in the news, but we wanted to understand the actual security benefits and researched the topic in detail. Our conclusion is that air-gapped communication offers little-to-no added hardware wallet security while degrading the user experience. In this article, we document our findings and check airgap security promises against published vulnerabilities.
Table of contents
What does airgap mean?
The myth of the unbeatable airgap security
Reality check: would airgap have saved you from these exploits?
Still, airgap can be useful
Usability is a cornerstone of security
Conclusion
What does airgap mean?
Airgap is a security measure that physically isolates a device from an untrusted network, like the internet, by removing all network interfaces. Air-gapped computers are used in security-critical infrastructure, for instance. This is a powerful principle in general, but usually data still needs to be exchanged with network-connected devices for regular operations. This data, which bridges the “air gap”, is commonly transferred using USB flash drives. The security of an air-gapped system fully relies on the fact that the exchanged data is not malicious or maliciously altered during transfer. As famously demonstrated by the Stuxnet malware that sabotaged an Iranian uranium enrichment facility, not thoroughly inspecting the exchanged data can render security benefits moot, for nuclear factories or for cryptocurrency hardware wallets.
With respect to cryptocurrency wallets, the term airgap has come to mean that a signing device like a hardware wallet (that protects the private signing keys) and a potentially insecure networked computer (that is used to create unsigned transactions and then broadcast the signed transactions) are physically isolated and not directly connected to each other. Any communication between the two devices needs to bridge the “air gap”, usually by physically exchanging an SD card, or scanning QR codes. Importantly, communication does and must exist. Such communication includes transactions as mentioned above, but also relatively large amounts of data for updating the firmware running on the hardware wallet or information about the wallet itself (e.g. public keys, aka addresses, for receiving coins).
Instead of plugging a hardware wallet into a computer, an air-gapped hardware wallet uses a companion software application installed on your computer that supports PSBTs (Partially Signed Bitcoin Transactions). You create an unsigned transaction in the application, which is either encoded in a QR code that you can scan with your hardware wallet, or the transaction is stored as a file that is then read by your hardware wallet, usually from a microSD card.
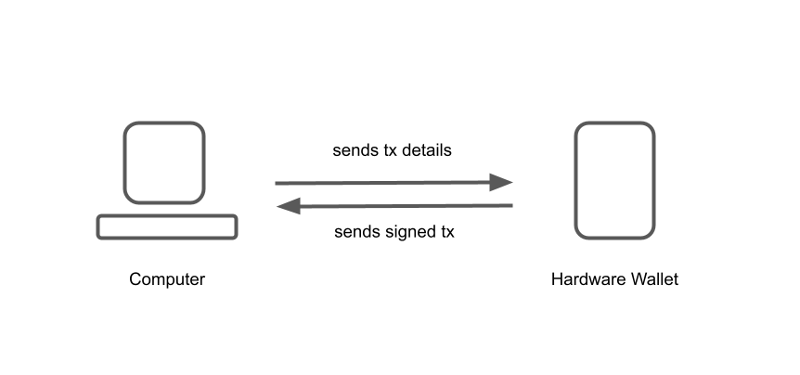
After the hardware wallet signs the transaction with the private keys, the hardware wallet then returns the signed transaction to the computer by either displaying it as a QR code on its display or writing another file onto the microSD card. The companion app on the computer imports the signed transaction and can then broadcast it to the network.
For perspective, while this blog post focuses on hardware wallet security risks and vulnerabilities, it is important to note that hardware wallets are widely considered to be the safest way to transact cryptocurrencies. This is because the private keys, which access and unlock your coins, are kept secured inside the hardware and do not need to leave the hardware wallet. On the other hand, software wallets are much more susceptible to theft from malware, while holding coins on exchanges bears its own set of risks. Alternatively converting an existing desktop computer into a dedicated air-gapped device, although sometimes recommended, is hard to secure and open to many attack vectors.
The myth of the unbeatable airgap security
Having no physical connection between the two devices makes it easier to perceive the connection as 'safe'. At the same time, plugging a hardware wallet into your computer the same way you would plug in a flash drive might not 'feel' as safe.

However, we came to the conclusion that the perceived security benefit, and how it is marketed as a silver bullet, greatly exceeds the reality of it and can lead to a false sense of security.
Here are the three main reasons why airgap does not do much for security in practice:
1. There’s still communication going on
Even though there is no physical connection in the shape of a USB cable, the wallet and host computer still exchange information. The difference between a wired connection and an air-gapped connection is mostly in their bandwidth. QR codes transport much less data than a USB connection. However, we found bandwidth is relevant for UX but not security, as described below.
Because Bitcoin transactions are really small in size, any of these communication channels are sufficient to transmit them. As taught by the Stuxnet example above, no communication channel by itself prevents the sending or receiving of data that is different than the expected bitcoin transaction data. Such data could be potentially malicious. It is therefore still the responsibility of the hardware wallet to thoroughly inspect and sanitize all data it receives.
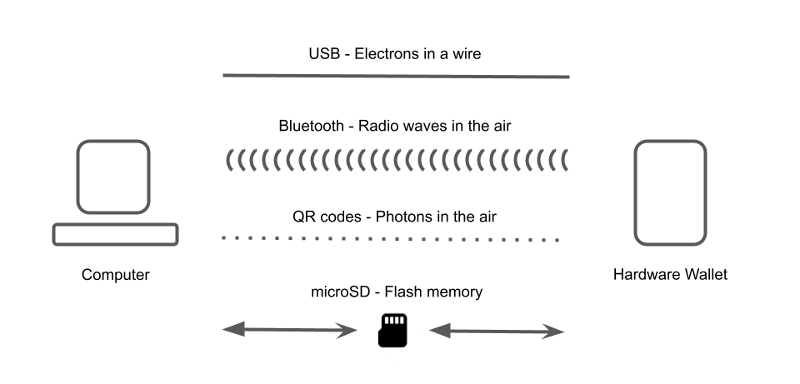
If the hardware wallet receives tampered data and does not verify it properly, being air-gapped or not does not matter at all. If an attacker was to find an exploit, the exploit could be loaded through a malicious QR code, a transaction file, or data transmitted through a USB connection or via Bluetooth.
Air-gapped transmission is really just another communication channel, even if the user is more manually involved. Every channel has its own attack vectors, and as long as information is exchanged, it’s always the hardware wallet that needs to do its job and sanitize it. Specifically, the hardware wallet threat model must assume the computer or phone it communicates with is compromised. Therefore, trusting anything other than what is displayed on the hardware wallet itself is a bad idea.
2. Communication can still be compromised
An important attack vector is malware that can tamper with the communication and alter it undetected. For example, it could alter a receive or change address, or swap out co-signers in a multisignature setup. Again, the hardware wallet firmware should be designed to catch that, but airgap in itself does not help:
- QR codes can be maliciously altered on multiple levels, including through backdoors introduced by an upstream library that controls camera images or rendering of QR codes, camera firmware, or by malware running on the host.
- With a microSD card, other programs could, for example, potentially monitor its content, alter PSBT files, or write additional data onto the card without the user noticing. The exact access privileges depend on the operating system used.
- USB communication itself similarly does not help mitigate this attack vector.
A common way to detect and avoid tampered data is to encrypt all communication between the companion app running on a computer and the firmware (the BitBox02 does this using the Noise Protocol Framework). Even then, this still does not provide a fully secure communication channel if the host computer running the app is compromised (which is why you should always verify transaction details on the hardware wallet’s built-in screen), but it makes it much harder for an attacker to eavesdrop or alter information.
3. Airgap is not more transparent for everyday use
Another promise of air-gapped wallets often cited is that the data shared between devices is more transparent and verifiable than it would be by using a USB connection.
"This more robust security model ensures that you know exactly what information is being received" -- Foundation Devices
“By using QR code transmissions, we have eliminated potential malware infiltration risks and delivered a level of transparency that just isn't possible with Bluetooth or USB.” -- Keystone
“Only QR codes are used to transfer data from the cold wallet, the QR code format is controlled, verifiable and transparent.” -- Ellipal
To evaluate the benefit of this claim, we’ll look at a simple Bitcoin transaction created with Sparrow wallet: it contains one input, one recipient, and a change address.
The wallet allows exporting the unsigned transaction in two ways:
1. PSBT files are stored in a binary format that is not human readable. You can’t open them and check the contents. The only way to do that is to load them into a Bitcoin wallet. So it’s the wallet again that has the responsibility to sanitize the data.
2. QR codes allow visually representing the same information. Because the transaction is too big for a single QR code, an animated code is used. Again, the information is not human readable, and another wallet is needed to verify the data.
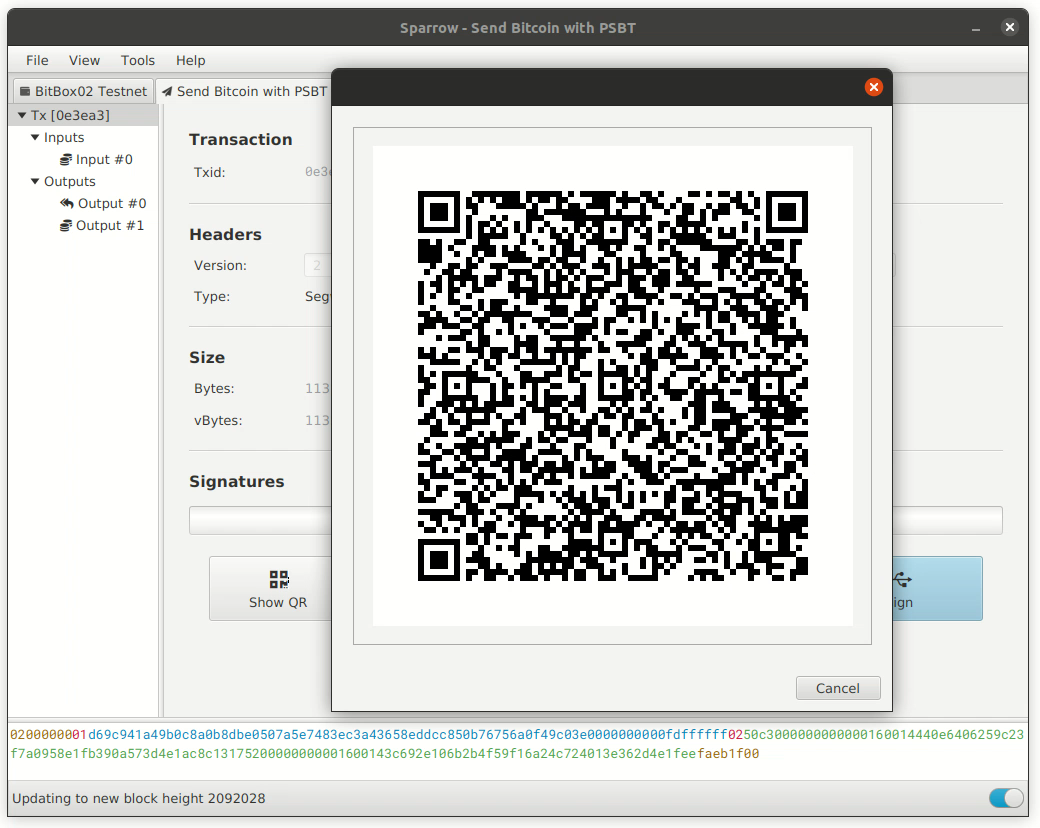
If you simply try to read the data with a regular QR code scanner, you’ll be none the wiser:

With both methods, it’s possible to verify the data not only on the intended hardware wallet but also using a different wallet. In our opinion, it’s doubtful that this adds a real security benefit (it’s the hardware wallets’ main job to sanitize the data and let you verify it on the built-in screen), and it’s unrealistic that users will do that on a regular basis.
Other things to consider
Every communication channel has pros and cons. Here are some additional considerations about hardware wallet communication methods:
- MicroSD cards contain a mini-computer (i.e. microcontroller), running firmware that can be hacked. Is it really air-gapped if you need to plug in a mini-computer into a hardware wallet to use it?
- External software library dependencies should be minimized to reduce the attack surface. That holds true for USB software drivers, but also for software drivers of microSD card readers and embedded cameras.
- Shoulder surfing and surveillance cameras viewing QR codes or text in an app impact privacy.
- Wireless communication modes such as Bluetooth and NFC broadcast identification information that can cause privacy concerns.
As with most things in life, there’s not “the one best option”.
Reality check: would airgap have saved you from any hardware wallet exploit since 2020?
Let’s examine all vulnerabilities since the beginning of 2020 that are known to us, limiting the scope to Bitcoin-related issues. The goal of this list is simply to check if air-gapped communication would have prevented the vulnerability.
Overall, not a single vulnerability we looked at relies on the data transportation layer, where information is exchanged between a hardware wallet and a computer or phone. This means that all these exploits can work whether a device is air-gapped or not.
If you’re interested in the vulnerability itself, we provide links with more details for you to get the full picture. None of the following vulnerabilities are known to have been exploited in the wild, and some are more theoretical and infeasible for other reasons.
- Supply chain vulnerability with attacker-controlled firmware (Coldcard, 2020/03)
Allows flashing malicious firmware and reset to a compromised “factory” state
Further reading by reporter, vendor
Airgap does not help: physical attack vector - OP_RETURN treated as change output (Trezor, 2020/03)
Allows to skip user confirmation, could affect level 2 protocols (e.g. Omni layer)
Further reading by vendor
Airgap does not help: transaction validation issue - Malicious Change in Mixed Transactions (Trezor, 2020/03)
Change could be sent to a 1of2 multisig address, partially controlled by an attacker
Further reading by reporter (Shift Crypto), second report (2020/03), vendor
Airgap does not help: transaction validation issue - Insufficient field size check (Trezor, 2020/03)
Transaction containing a `prevhash` exceeding the expected 32 bytes could contain a hidden output sending funds to attacker
Further reading by vendor
Airgap does not help: transaction validation issue - Inconsistent sanitization of transaction inputs (Trezor, 2020/03)
Transaction with single-sig input and a 1of2 multi-sig output (partially controlled by an attacker) would be accepted without the appropriate user verification.
Further reading by vendor
Airgap does not help: transaction validation issue - Large Transaction fee via two Segwit transactions (all vendors, 2020/03)
Malicious wallet could trick user into signing a Bitcoin transaction twice, e.g. by faking an error after first signing, asking the user to try again, and creating a transaction with a huge mining fee. Collaborating with a miner could allow access to these fees.
Further reading by Shift Crypto, Ledger, Trezor, Coinkite
Airgap does not help: general verification design issue of BIP-143 - JTAG/SWD enabled on unsecured processor (Ledger, 2020/06)
The Ledger Nano X MCU had its debug interfaces enabled. This could effectively allow a supply chain attack, but not access to internal secrets.
Further reading by reporter, vendor
Airgap does not help: physical attack vector - Bitcoin derived fork/altcoins cross-account signing (Ledger / Trezor / Keepkey, 2020/08)
User can be tricked into signing a Bitcoin transaction while the device shows testnet or altcoin details on screen.
Further reading by reporter, Ledger, Trezor
Airgap does not help: transaction validation issue - Bitcoin mainnet/testnet cross-account signing (Coldcard, 2020/08)
User can be tricked into signing a Bitcoin mainnet transaction while the device shows testnet details on screen.
Further reading by reporter (Shift Crypto), vendor
Airgap does not help: transaction validation issue - Ransom attack on passphrase handling (Trezor/Keepkey, 2020/08)
A wallet created with a passphrase on the host computer allows malware to use a different passphrase on the hardware wallet and hold all future funds ransom.
Further reading by reporter (Shift Crypto), vendor
Airgap does not help: passphrase must be entered or verified directly on device regardless of communication channel - Remote multisig theft attack (Coldcard, 2020/11)
The device did not check if it was part of a newly created multisig wallet, allowing an attacker to trick the user to create an attacker-controlled multisig wallet.
Further reading by reporter (Shift Crypto), vendor
This is a general wallet verification issue when receiving malicious data from an external coordinator or a 3rd party participant:
- This vulnerability can be mitigated if the multisig wallet is set up fully by yourself, simply by passing a microSD card from hardware wallet to hardware wallet. This also holds true if the devices communicate with each other via QR codes or USB (although nobody implemented this yet).
- Airgap does not help if the multisig wallet is set up with an external coordinator or with a different (malicious) person serving as a co-signer, even if the device is fully air-gapped. - Length-extension attack on SCP (Ledger, 2021/05)
Allows an attacker to decrypt a block of application data and firmware updates, without any security impact (data is not secret and is publicly available).
Further reading by vendor
Airgap does not help: data can be read anywhere when downloading new firmware
These are all the relevant and publicly disclosed hardware wallet vulnerabilities that we know of. Sources (also covering older vulnerabilities): Shift Crypto, Ledger, Trezor, List of Hardware Wallet Hacks
Of older attacks, the closest relevant example we could find was reported in 2018 as a potential data leak when using U2F (universal second-factor authentication). However, this example is also not about the USB transport layer but how U2F data is encoded (i.e. parsed) prior to passing it through USB.
Outside of invasive attacks requiring physical possession of a hardware wallet, vulnerabilities typically exploit the logical layer, where the hardware wallet fails to verify or correctly parse transaction details.
In addition, it’s important to realize that airgap cannot protect you against malicious firmware. There are countless possibilities to leak private keys if the hardware wallet itself is compromised (e.g., through Bitcoin signatures).
Still, airgap can be useful
Airgap integrations
Communication methods like QR codes or microSD cards can be useful for other reasons, such as convenience and UX, depending on the devices involved:
- When communicating via QR-codes or microSD cards using the PSBT standard, third-party apps can be more easily integrated and mixed-and-matched with hardware wallets.
- QR codes are a convenient communication choice for general-purpose hardware that can make use of an easily connected camera add-on, like Seedsigner or Specter DIY, for example.
- QR codes are helpful when communicating with a device that restricts usage of USB connectivity, like the Apple iPhone.
Note that while “PSBT” is sometimes used synonymously with “airgap”, it is instead a standard to move unsigned transactions to another device for signing, independent of any given communication method. This enables interoperability between multiple devices and software wallets, which is a compelling reason to support PSBT natively.
"No communication" security
From a security perspective, the one good use case we identified is using the hardware wallet with “complete” airgap without receiving external communication. Importantly, this is not about “air-gapped communication” as conventionally defined in the hardware wallet space, but about “no communication” from an untrusted device. While this is obvious in theory, a practical example is the "Remote multisig theft attack" as explained above. However, “no communication” isn’t possible all the time: to prepare and ultimately broadcast a transaction, you need external data about how many coins you currently possess and where to send them.
"No communication" operations can reduce the attack surface for operations where no external information is necessary, such as creating or recovering a wallet seed, generating receive addresses, naming a wallet, enabling/disabling an optional passphrase, etc. Of course, "no communication" operations could be implemented on any hardware wallet, even those not advertised as air-gapped, for example when running off a power bank to display a receive address on the hardware wallet's screen.
Air-gapped communication can limit potential attacks that require consecutive communication to the hardware wallet, for example that continuously probe the device. A hardware wallet, however, is purpose-built with a strict communication protocol, simply aborting any connection that does not follow the rules. Compared to other security challenges, implementing a strict communication protocol is straight-forward, and we’re not aware of such probing attacks being successfully demonstrated.
Usability is a cornerstone of security

Using an air-gapped hardware wallet comes with significant usability sacrifices. It takes more steps, button pushes, mental attention, and time to send a transaction involving a PSBT over an air-gapped communication channel.
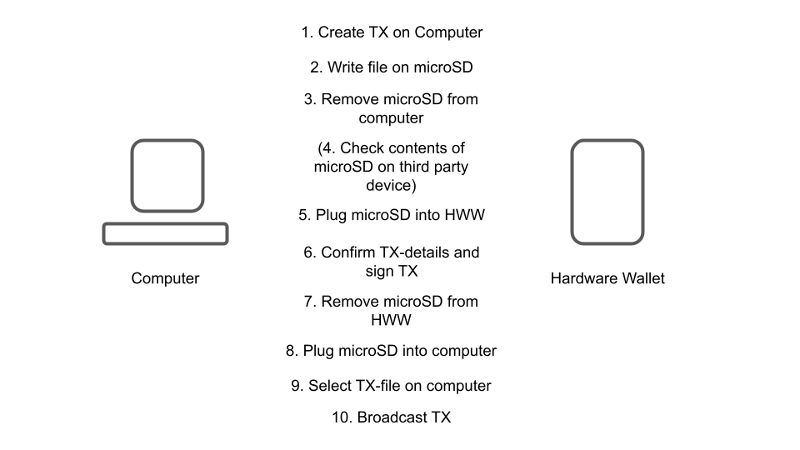
The user becomes part of the communication channel, they’re essentially a man-in-the-middle, without a good way to audit what data they are relaying. This adds friction without a clear security benefit.
An air-gapped device needs to pack much of the user interface into the firmware. Anything other than the most basic operations is easier to do with an external desktop or mobile application, with the hardware wallet connected to it.
This is why we not only produce hardware but created the beginner-friendly BitBoxApp that makes using the BitBox02 very accessible. By having strict transaction verification rules, a rigid USB communication protocol, and end-to-end encryption, the BitBox02 is able to secure the communication channel while offering a simpler user experience.
In addition, future important security or privacy protocols can further complicate the airgap UX. An example is the ‘anti-klepto’ protocol that is designed to protect against leaking a user’s private key, which was first implemented in the BitBox02. Another round of exchanging information between the hardware wallet and the computer protects against malicious manipulation of a transaction signature. If an air-gapped device would implement this security mechanism, the process of sending a transaction would require the user to do another round of manual QR code scanning.
Conclusion
So what does this mean for hardware wallet manufacturers making design decisions and users making purchasing decisions? In our opinion, picking a communication mode is a UX and app integration choice rather than a security consideration, at least from a technical point of view.
Of course, if a given market "feels" like a certain mode of communication is better than others, satisfying this need can make business sense. That said, while over-promising happens often in marketing, it can mislead users and in the end damage the overall perception of the industry. Therefore, helping to "keep each other in check" about marketing claims is in everyone's best interest.
A common saying is "complexity is the enemy of security". In other words, making the UX as simple as possible is a security benefit in terms of making it harder for a user to shoot themselves in the foot. When we designed the BitBox02 two years ago, we felt a USB male connection that can directly plug into new computers and mobile phones would give users the best experience without sacrificing security. Our research into airgap communication documented in this article shows that our decisions have stood the test of time.
Another common saying is "there's a tradeoff between security & ease of use". However we believe this is a false dichotomy, and the purpose of a hardware wallet is exactly to make security easy. Our cutting-edge security model has been praised by experts and helps users to not have to worry about someone else unlocking their coins. We designed the BitBox02 and BitBoxApp in a way that abstracts complexity away from the user. We do include advanced feature options, which most people might not even expect in the beginning but will value over time, as they continue their journey to financial independence. Examples include the direct connectivity to your own Bitcoin full node, better privacy protection by using the Tor network, coin control, and many more.
This article challenges the current conventional thought in the field, and so we understand it may be taken as a controversial viewpoint. We are happy to hear differing viewpoints, and we’ll continue to explore the topic ourselves in the future. So let us know what you think.
Frequently Asked Questions (FAQ)
What does "airgap" mean in terms of hardware wallets?
Airgap is a security measure that physically isolates a device from untrusted networks, like the internet. In cryptocurrency wallets, it means the signing device and the networked computer are not directly connected, usually communicating via QR codes or SD cards.
Does airgapping a hardware wallet make it more secure?
While airgapping can offer some security benefits, the article concludes that air-gapped communication offers little-to-no added hardware wallet security while potentially degrading the user experience.
Can airgap protect against all vulnerabilities?
No, many vulnerabilities exploit the logical layer of hardware wallets, where the device fails to verify or correctly parse transaction details. These vulnerabilities can exist regardless of whether a device is air-gapped.
Is there any advantage to using airgap?
Airgap can be useful for certain UX and app integration choices. For instance, QR codes can be convenient for devices with camera add-ons, and PSBT enables interoperability between devices and software wallets.
What's the main takeaway regarding airgap and hardware wallets?
Choosing a communication mode for a hardware wallet is more about user experience and app integration than security. It's essential to ensure that the chosen method doesn't compromise security while offering a good user experience.
Shift Crypto is a privately-held company based in Zurich, Switzerland. Our team of Bitcoin contributors, crypto experts, and security engineers builds products that enable customers to enjoy a stress-free journey from novice to mastery level of cryptocurrency management. The BitBox02, our second generation hardware wallet, lets users store, protect, and transact Bitcoin and other cryptocurrencies with ease - along with its software companion, the BitBoxApp.

