Du kannst auch die deutsche Version dieses Artikels lesen.
If you’re reading this, chances are you own some bitcoin or other cryptocurrencies. Chances are also quite high that you never really thought about what happens to these assets if you get hit by a bus (I hope you’re not reading this on your phone while walking).
The goal of this article is to get you thinking about exactly that, motivate you to get a simple inheritance plan in place and provide you with further reading if you want to do it even better.
Securing digital assets like bitcoin is a fascinating challenge. If you want to own your assets, you need to be in control of your own private keys. We recommend using a hardware wallet like the BitBox02 for that, but whatever wallet you choose, there is some sort of secret (like a backup, a password or a seed phrase) that you cannot delegate away. Whoever gains access to that secret has full control over your funds.
The temptation is to split this secret, make it less accessible, distribute or bury it somewhere. But that only creates a new issue: will it still be accessible if I am no longer around? Will my loved ones be able to retrieve it? Or will my funds be lost forever?
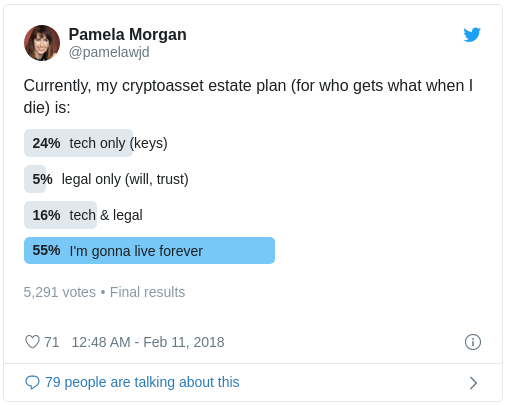
Nobody likes to think about their own death:
Still most people don’t want their digital assets to be lost. The goal of an inheritance plan is to ensure that your heirs will be able to access your digital assets at the appropriate time, but not before. The main challenge is to strike a balance between security and accessibility that works for you and your situation, without exposing your assets to the risk of theft.
The best way to make an inheritance plan is to write a “Letter to loved ones”, as recommended by Pamela Morgan, author of Cryptoasset Inheritance Planning. The goal of this letter is to make your loved ones aware that you own bitcoin or other cryptocurrencies and make sure these assets can be recovered without you. The letter doesn’t contain any secrets, so reading it won’t enable anyone to steal your assets. But it contains private financial information, so you should still treat it confidentially.
A minimal plan is better than no plan. Why not start now?
Step 1: Trusted people to assist
Imagine your loved ones reading your letter and realizing there are bitcoin to be recovered. Remember your first time installing wallet software, setting it up and sending transactions? It’s quite stressful and there are many things that could go wrong.
The biggest help you can provide your heirs is to name multiple people who have experience with cryptocurrencies, and that you know and trust in real life. When your heirs access your funds with the information you provided, it’s best if there are at least two trusted people present, who don’t know each other, and that can monitor and question every step independently.
Write down three people that you think fit the profile, including contact details like phone number, email or Twitter handle.
Step 2: Secure storage
Think about where you can securely store secrets. Of course “securely” is relative and should depend on the total worth of the assets you want to protect. Possible options range from a locked drawer, to a home safe, to safe deposit boxes.

To recover your assets, you should rely on proper, verified backups. If you already have backups of your digital assets, it’s ok to stick to your current locations and maybe upgrade your security later.
If you don’t have a backup of a wallet yet, create it when you are documenting the wallet. Write it by hand on a separate piece of paper, store it in a secure location and note that location in the inventory (see step 3).
There are various ways to split up a backup so that you don’t need to store it in a single place and a thief would need to get to multiple locations. We’ll look at these at the end.
Step 3: Inventory
It’s important that your heirs know what to look for physically. An inventory ensures that they know where to find your backups. It will also give them the peace of mind that they did not miss “the big stash” buried somewhere.
Now let’s create a quick inventory of your digital assets. The key is not to write down any secrets, but to note where your backups are stored. Also, don’t write down any amounts, as they become outdated very quickly and might leave your heirs guessing where the rest is.
Important: it is ok to write your inventory on a computer, but do not store any of the secret access information electronically. Take a piece of paper and write the information by hand. And no pictures with your smartphone!
Optional for advanced users: you can also include the extended public key in the inventory. However, I would advise against including links to block explorers or create QR codes online, as this would be a serious privacy leak.
Phone
Do you have wallet apps installed on your mobile phone? Let’s start with that. Make sure you have an external backup of every wallet, preferably by writing down the mnemonic seed on a separate piece of paper by hand. You can use our "print yourself" Backup Card.
Note the following details for each mobile wallet you have:
- Make and model of your mobile phone (e.g. “Samsung Galaxy S10, blue”)
- Name of wallet app, with the corresponding assets (“Green Wallet: BTC”)
- Secure storage location of access information (“at home, locked top drawer”)
Computer
Document all digital assets that you hold in software wallets (like Electrum) or local client-side browser wallets (like MyEtherWallet or Metamask) and that are not secured by a hardware wallet.
Note the following information:
- Make and model of your computer (e.g. “Acer Swift 7 laptop, orange”)
- Name of wallet application, with corresponding assets (“MyEtherWallet: ETH, MKR)
- If applicable, number of accounts of the same currency
- Secure storage location of access information (“safe deposit box at XYZ”)
Custodial wallets
If you keep funds on exchanges or on custodial web wallets, things are a bit more complicated. While it might be ok for your heirs to login to a pure web wallet and move the funds to a new wallet, selling your assets and withdrawing to a regular bank account under false credentials can cause legal issues.
Depending on your legal assessment, include in the access information either the full login credentials or the contact information of the custodian:
- Name and URL of web wallet or exchange (e.g. “BTCX, www.btcx.com”)
- Assets (“BTC, ETH, USD”)
- Contact or inheritance information (“on Support, search for <death>”)
- Optional: Secure storage location of login details, incl. 2FA details if necessary
Hardware wallets
For larger amounts, the best way for most people is to use hardware wallets. If your heirs have the device at hand, it’s easy to just use it as-is. For that they need to have the companion app and the device password / PIN. Additionally, you should write down the mnemonic seed, which allows them to recover all funds even without the device.
Note the following information:
- Name and make of the hardware wallet (e.g. “BitBox02”)
- Assets (“BTC, ETH, DAI”)
- If applicable, number of accounts of the same currency
- Secure storage location of device password / PIN (“at uncle Marty”)
- Secure storage location of mnemonic seed (“in bank vault”)
- Optional: passphrase (“at aunt Pam”)
Custom storage solutions
When using other cold storage solutions, make sure to document these as well. If they don’t follow a well-documented standard (e.g. the Glacier protocol), it’s your responsibility to document it.
Step 4: Finishing up (for now)
You now have a list of trusted contacts, a handwritten inventory and (potentially) some new backup papers. Now, let’s put that all together in the “Letter to your loved ones”.
Have a look at the following templates and with the information at hand, use them to write your own letter, or adapt them to your liking:
- English template by Pamela Morgan: Letter to Loved Ones
- German letter generator by Marc Steiner: Bitcoin Nachlass-Tool
An important point to mention in the letter is that your loved ones should think about what they want to do with your bitcoin before they attempt to gain access.
- Do they want to hold on to them? Then they should familiarize themselves with how to set up a hardware wallet and have one ready to take over the funds.
- Do they want to sell them? Then they should already set up an exchange account, do all the KYC and secure the account with password and a second factor.
- Once sensitive information like a mnemonic seed has been restored, all funds should immediately be moved to a new hardware wallet or exchange. Otherwise, every person involved in the process could access and move the funds after that, even remotely.
Put your various papers in envelopes, seal and sign them, including the date. For backups, make sure to note the designated secure storage location on the envelope.
- Letter to loved ones, including trusted contacts: keep somewhere private, where it will be found
- Backups: distribute to secure storage locations as soon as possible
Splitting up secrets
You might be uncomfortable storing the full access information to your digital assets in a single place. And you’re right, depending on the amount secured that is not advisable. Security can be improved significantly by splitting up the access information.
But complexity is the enemy of security. Which in this context is even more true, as the danger of making critical mistakes is significantly increased by the inexperience of the people recovering your bitcoin. How does that translate to common solutions?
- Passphrase: in addition to writing down the 12 or 24 words (the “mnemonic seed”), wallets can be protected with an additional passphrase. If you are using a very long, random passphrase (at least 14 characters, upper and lower case characters and numbers), this is probably the best option to split the access information in two places (mnemonic seed in one place, passphrase in a different place).
- Split mnemonic seed: If your mnemonic seed has 24 words (and only then! see what happens if you do that to a 12 word mnemonic seed), it is secure enough to split it into three individual cards with each card missing 8 words. You can set this up in a way that a minimum of two cards are necessary to restore the mnemonic seed, while still preserving enough entropy (~80 bits) for it to be secure. This level of security might not last for decades, however, as the efficiency of brute forcing a mnemonic seed increases steadily.
Card 1
XXX w02 w03 w04 w05 XXX XXX w08 XXX XXX XXX XXX
w13 w14 w15 w16 w17 w18 w19 w20 w21 w22 w23 XXX
Card 2
w01 XXX XXX w04 XXX w06 w07 w08 w09 w10 w11 w12
w13 w14 XXX w16 w17 w18 XXX XXX XXX XXX w23 w24
Card 3
w01 w02 w03 XXX w05 w06 w07 XXX w09 w10 w11 w12
XXX XXX w15 XXX XXX XXX w19 w20 w21 w22 XXX w24- Multisignature solutions are tricky and must be documented in detail. See our blog post The pitfalls of multisig when using hardware wallets and decide for yourself if these risks can be mitigated reliably.
- Shamir’s Secret Sharing is a reliable and secure way to split a secret into multiple parts. It can be used to split a mnemonic seed, but doing that securely is not easy. Especially the secure recovery is tricky, with many pitfalls and it should happen completely offline. Research and document thoroughly. Make sure an appropriate recovery environment is available, e.g. instructions and a USB flashdrive with Tails.
Going forward
This blog post was a bit lengthy, but I wanted to make sure that every step is crystal clear. The process itself is not complicated and the time you invest is certainly worth it in the long run. It helps getting your personal backups in order, make sure they are recoverable by you and — at the appropriate time — by your loved ones. And it will hopefully encourage you to revisit your backups from time to time, check if everything is still in order and update the details if necessary.
Further reading
- English: Cryptoasset Inheritance Planning by Pamela Morgan
- German: Kryptos verwahren und vererben by Marc Steiner (planned)
BitBox backup solutions
With the BitBox02 hardware wallet you have everything you need to properly secure your funds. But how can you improve the security of your backup? We have thought of a few additional options depending on your specific needs.
You can find more details on our Backup solutions page.
Check out our online store, we ship worldwide!
Frequently Asked Questions (FAQ)
Why is it important to prepare my bitcoin for inheritance?
It ensures that your loved ones can access your bitcoin assets in the event of your sudden demise, striking a balance between security and accessibility.
What is the primary challenge in bitcoin inheritance planning?
The main challenge is to ensure your heirs can access your bitcoin at the right time without exposing the assets to theft risks.
What is the "Letter to loved ones"?
It's a letter that makes your heirs aware of your bitcoin holdings and provides guidance on recovering them without revealing any secrets.
How can I assist my heirs in accessing my bitcoin?
By naming multiple trusted individuals experienced with cryptocurrencies to guide them through the process.
Why is splitting up access information advisable?
It enhances security by ensuring that full access to your digital assets isn't stored in one place, reducing theft risks.
Shift Crypto is a privately held company based in Zurich, Switzerland. Our international team of specialists across engineering, cryptosecurity and Bitcoin core development build the BitBox products and provide consulting services. The BitBox02, a second generation hardware wallet, equips individuals to easily store, protect, and transact cryptocurrencies. Its companion, the BitBoxApp, provides an all-in-one solution to securely manage your digital assets with ease.

