Hardware wallets are the most secure way to store, send and receive bitcoin. But they haven’t always been as secure as they are today. While early designs improved upon the security of software wallets, they were often still very much reliant on the security of the host device, e.g., your computer or phone.
Throughout the years, security researchers found multiple vulnerabilities that might seem obvious in hindsight, but as the concept of hardware wallets wasn’t as mature as it is today, these flaws were not discovered for years.
Let’s look at these vulnerabilities, learn how they work, and how the BitBox02 fixes them. For the sake of understanding, some examples are simplified.
Unvalidated change output
Bitcoin transactions don’t just contain a sender and a receiver address. Since Bitcoin uses the UTXO model, transactions can only be spent as a whole. This requires them to have a change output, which is sent back to an address owned by the sender. This works similarly to cash, where the merchant gives you back your change.
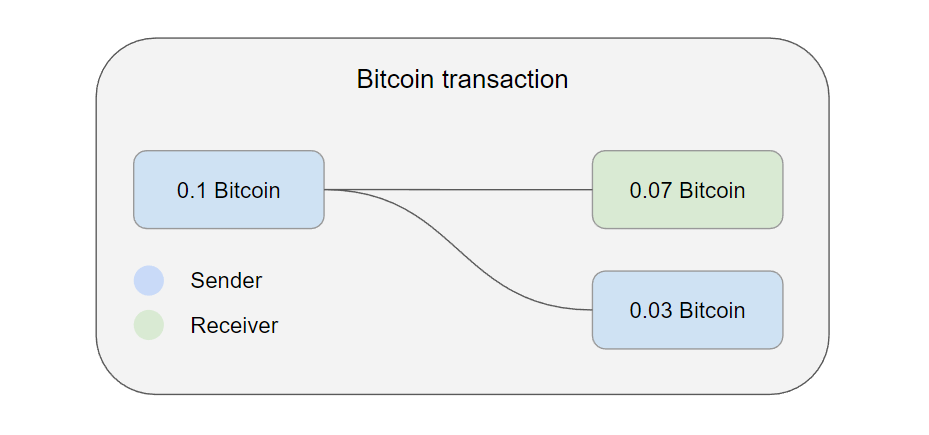
Some hardware wallets did not check correctly if they are the receiver of this change output. Because the hardware wallet screen only shows the transaction amount without the change output (labeled green in the diagram), an attacker with access to the host device could simply add multiple UTXOs as inputs and divert the change output to an address controlled by them, thereby stealing much more than the hardware wallet will show as a transaction amount.
The BitBox02 fixes this issue by verifying that the change output is actually an address that’s part of the wallet. If an attacker tries to inject their own address as a change output, the BitBox02 will simply reject the transaction.
Passphrase entry on the host device
Hardware wallets usually don’t come with a lot of buttons. Entering a BIP39 optional passphrase on a device with two buttons can be quite tedious, as passphrases can (and should) contain numbers, letters, and special characters.
To make entering the passphrase easier, some hardware wallets let the user enter it on the host device, which then sends it to the hardware wallet. This in itself negates some of the security benefits of using a passphrase, as the host device learns the passphrase, which is part of your backup. But this makes a much worse attack possible:
Entering your passphrase on a malicious host device allows an attacker to secretly pass a different passphrase to your wallet. Everything will work as you expect until you try to send a transaction. The attacker can hold your coins for ransom and might only give out the correct passphrase after you have paid them.
The BitBox02 prevents this attack by using more available buttons and therefore allowing the user to easily input their passphrase on the hardware wallet itself. The host device never learns the passphrase.
Tampered multisig cosigners
Multi-signature wallets are generally used to increase the security of holding bitcoin. Instead of using a single hardware wallet, a multisig wallet requires multiple (hardware) wallets to sign a transaction or to create a receiving address.
To generate a bitcoin receiving address, the extended public keys (xpubs) of all wallets are necessary. Therefore, the hardware wallet asks the host device for the xpubs of the cosigners.
Trusting the host device to provide the xpubs of the cosigners is dangerous. If the host device is compromised, an attacker can swap out the xpubs of the actual cosigners with some that are controlled by the attacker. As the hardware wallet can only verify its own xpub, it cannot detect this change. The bitcoin address that’s shown on the hardware wallet screen is a valid address, but not controlled by the victim because the attacker controls the majority of the cosigner keys.
The BitBox02 saves the metadata of the multisig wallet on the device itself. This means it can fully validate the multisig wallet parameters, detect if the xpubs have been altered, and warn the user. Nowadays, most modern hardware wallets prevent this type of attack.
Excessive fee rate
Another way that a compromised host device can attack a hardware wallet is by changing the fee rate that the user sets for a transaction. When the host device sends the transaction data to the hardware wallet to review and sign, instead of using a reasonable fee rate, it passes along a fee rate that is many times more expensive. This can be set high enough to drain the entire wallet (think of a 1 Bitcoin transaction fee).
Because the attacker doesn’t earn the transaction fee, instead of broadcasting this signed transaction, the attacker blackmails the victim. If they don’t pay the attacker a certain amount of money, he will broadcast the transaction and the money of the victim will effectively be burned. Attempts to spend the money before the attacker will most likely fail because the high fee rate will make it much more likely that the malicious transaction will be included first. Alternatively, the attacker could collude with a miner and split the excessive transaction fee with them.
As an easy fix to this attack, the BitBox02 shows the transaction fee on its own display. The user can verify that the transaction fee has not been altered. It will even warn the user if the fee is unreasonably high (more than 10% of the transaction amount).
Isolation bypass
Hardware wallets are often used to store multiple cryptocurrencies at once. This is comfortable, but can also lead to problems. Since some currencies share a similar address format and derivation path, a wallet can be tricked into sending a transaction spending the wrong currency.
This can for example mean that a user signs a transaction for mainnet-Bitcoin instead of testnet-Bitcoin, or Ethereum instead of a similar, less valuable fork. An attacker can hold this transaction ransom and blackmail the user with it. If the user doesn’t pay the ransom, the attacker broadcasts the transaction, sending away the user’s funds.
To prevent this attack, the BitBox02 uses distinct derivation paths for different currencies and also shows the currency on the device when signing a transaction.
Conclusion
As is evident by these examples, hardware wallets are still evolving and becoming more secure every year. This is why the active development of the hardware wallet firmware, regular updates, and a bug-bounty program to incentivize responsible security disclosures are so important.
Luckily, although these attacks have been found and reported, there have been no public records of people falling victim to any of these attacks.
As long as most people store their money on exchanges and vulnerable software wallets, attacking these centralized providers still proves to be more efficient than attacking individual people.
Frequently Asked Questions (FAQ)
Are hardware wallets secure?
Yes, hardware wallets are the most secure way to receive, store and send bitcoin. There have been vulnerabilities in the past, but there is hardly any evidence of these vulnerabilities being abused by attackers.
How can I make sure my cold wallet doesn't get hacked?
In order to stay secure, you should keep your hardware wallet updated. Make sure your wallet is running the latest firmware. If your device is old and unsupported, consider upgrading to a modern one.
Can I use my hardware wallet wrong?
A good hardware wallet will make it very hard to use it in a wrong way. But its security still relies on the user checking certain information manually, such as bitcoin addresses or the transaction fee. If you are unsure how to use your wallet correctly, you should check the official user manual.
What are the vulnerabilities of early hardware wallets?
Early hardware wallets, while more secure than software wallets, had vulnerabilities. These included unvalidated change outputs, passphrase entry on the host device, tampered multisig cosigners, excessive fee rates, and isolation bypass.
How does BitBox02 address the change output vulnerability?
BitBox02 verifies that the change output is an address that’s part of the wallet, preventing attackers from diverting the change output to their own address.
Why is entering a passphrase on the host device risky?
Entering the passphrase on the host device exposes it to potential attackers. BitBox02 allows users to input their passphrase on the hardware wallet itself, ensuring the host device never learns it.
How does BitBox02 ensure multisig wallet security?
BitBox02 saves the metadata of the multisig wallet on the device. This allows it to validate the multisig wallet parameters and detect if the extended public keys have been altered.
What measures does BitBox02 take against excessive transaction fees?
BitBox02 displays the transaction fee on its own screen, allowing users to verify it. It warns users if the fee is unreasonably high, such as more than 10% of the transaction amount.
How does BitBox02 prevent currency confusion in transactions?
BitBox02 uses distinct derivation paths for different currencies and displays the currency on the device when signing a transaction, preventing users from accidentally sending the wrong currency.
Don’t own a BitBox yet?
Keeping your crypto secure doesn't have to be hard. The BitBox02 hardware wallet stores the private keys for your cryptocurrencies offline. So you can manage your coins safely.
The BitBox02 also comes in Bitcoin-only version, featuring a radically focused firmware: less code means less attack surface, which further improves your security when only storing Bitcoin.

Shift Crypto is a privately-held company based in Zurich, Switzerland. Our team of Bitcoin contributors, crypto experts, and security engineers builds products that enable customers to enjoy a stress-free journey from novice to mastery level of cryptocurrency management. The BitBox02, our second generation hardware wallet, lets users store, protect, and transact Bitcoin and other cryptocurrencies with ease - along with its software companion, the BitBoxApp.

