Security on every level
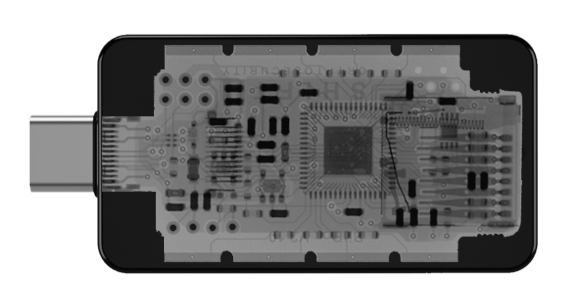
BitBox hardware wallets began in 2015, and every enhancement and security improvement has led to the BitBox02 and BitBox02 Nova available today. The BitBox's hardware and software were built from the ground up, prioritizing security, with multiple external security teams reviewing its design and implementation.
All of our products are Swiss made and developed by our team of Bitcoin and crypto experts. You can help protect your financial sovereignty with the security features listed below.